
Verizon Admits Its Default DSL and FiOS Wireless Security "Does Not Provide Good Protection Against a Hacker"
AN OPEN MEDIA BOSTON INVESTIGATIVE REPORT. Verizon's default wireless security for subscribers to its FiOS Internet and DSL High Speed Internet service has been shown to include several critical security flaws and weaknesses that Verizon phone support agents do not disclose to its customers. These weaknesses are exacerbated by poor training and installation practices that leave users vulnerable to network infiltration, identity theft and data loss.
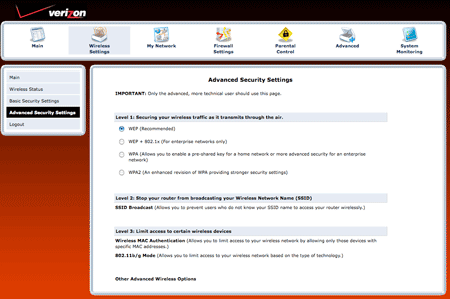
By default, the wireless routers Verizon provides to its FiOS Internet and DSL High Speed Internet customers have Wi-Fi enabled and utilize the WEP encryption specification, which has been unsecure since 2001 when it was first compromised. As Open Media Boston has previously reported, the free open source application Aircrack-ng can crack WEP encrypted networks in just a few minutes. Because of this, almost all modern wireless devices support the encryption specifications WPA and WPA2.
Due to its compromise, WEP encryption will not prevent an attacker from joining a wireless network.Aircrack-ptw co-author Ralf-Philipp Wienmann has stated, "WEP as a security measure is so broken that your (and everyone else's) kid sister can easily circumvent it" using a cracking tool.
According to Verizon FiOS Internet Media Relations manager Cliff Lee, Verizon uses WEP by default "mainly to prevent accidental use of the router, for example to stop a neighbor’s network devices from automatically connecting up to (and using) a customer's WiFi network." In reality, "accidental use" typically does not constitute a security threat, but rather a misunderstanding. Anyone intending to access a Verizon customer's router without permission can do so easily if that router's default settings are not changed.
While the Actiontec routers in question do support WPA and WPA2 (Actiontec's own support page indicates "the best choice for security is WPA Personal"), users would need to manually change the encryption specification in their router's settings and many novice computer users are unlikely to do this. Additionally, Verizon does not offer technical support for customers who choose these more secure specifications.
To understand the customer support experience of a user with security concerns but limited knowledge, Open Media Boston called Verizon's FiOS support line, in the actual capacity of helping a family member who is a FiOS customer, and requested support for setting up a new Actiontec FiOS wireless router the customer had requested to replace a malfunctioning router. Below are excerpts from that conversation and the full audio recording.
Open Media Boston: I think we were digging through his old router's security stuff and it looked like it only had a WEP password, and so I was wondering is that secure enough?
Verizon Support: Ok, the wireless is encrypted. Ok, it's a ten character encryption code for the WEP key.
OMB: That's the WEP.
Verizon Support: That's the WEP key. But you still need a firewall. The router has a firewall, but that protects only up to a certain point. And you really still need a firewall in each computer...
OMB: Yeah, I think...
Verizon Support: ...If you really want to be secure.
[Later in the conversation.]
Verizon Support: The WEP key... The WEP key's primary purpose is to keep strangers outside the home from hacking into your broadband and using your service.
OMB: But you said that's encrypted. So that's a... You said a ten character...
Verizon Support: That's right, a ten character encryption. You're right.
OMB: So people can't get onto the network?
Verizon Support: You can't guess the... Yeah, it's pretty hard to guess that.
OMB: Ok. So, like neighbors or someone walking down the street. That keeps them from getting on?
Verizon Support: No, I told you... Somebody... Yeah, yeah, that's right. Somebody sitting in their car with a laptop cannot jump on his wireless connection.
OMB: They can't jump on?
Verizon Support: Nope, nope.
[Later in the conversation.]
Verizon Support: The, the firewall... The firewall is, is to keep hackers from getting onto your system 'cause hackers pretty much, sometimes get around even WEP keys. But the firewall is to stop them from getting on.
OMB: Wait, wait, wait. Hackers can around the WEP key?
Verizon Support: Uh, hackers can get around anything.
OMB: Do, do you think... I mean, like what's the chance of them getting around that?
Verizon Support: ...They're, they're not looking for you and I. They're not looking for you and I. You know? They're looking for government cracks. They're looking for corporations to crack.
Hear the full conversation:
Lee admitted to Open Media Boston that "although WEP provides security to block unintentional connections, it does not provide good protection against a hacker who is actively seeking to attack a WiFi network." As indicated in the support call, though, when Open Media Boston asked repeatedly if WEP was secure, the support agent insisted it was. And although the agent finally admitted WEP was vulnerable, he did not demonstrate an accurate understanding of the vulnerability, attributing the weakness to keystroke loggers, rather than packet sniffers, and downplayed the threat. Understanding the caller was concerned with security, later in the conversation, the support agent informed Open Media Boston that Verizon offers an Internet Security Suite for $5.99 a month. While this software includes firewall, antivirus and antispyware protection, it does not change the default WEP key or switch the encryption protocol to WPA or WPA2.
No Cracking Tools Are Needed
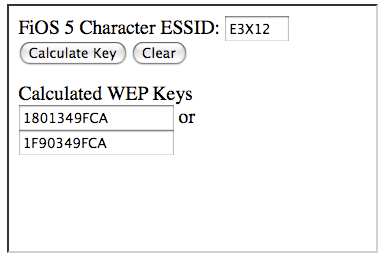
In fact, due to a recently discovered security vulnerability in Actiontec's default SSID and WEP key, attackers need not use Aircrack or, indeed, any software not already included in Windows, Mac or Linux computers to compromise an Actiontec MI424WR router Verizon provides to its FiOS customers. Security researchers Craig Heffner and Derek Yap discovered a direct link between the router's MAC address and its default WEP key, which "allows an attacker to instantly, and completely passively, obtain the network's WEP key." (View the full PDF report on the SourceSec Security Research site.)
According to security researcher Kyle Anderson, "One needs two pieces of information to decrypt the WEP key like this: the SSID and the MAC. You actually already have both of these as soon as you 'see' the access point in your list of nearby wireless access points." With some math help from Fred Williams, Anderson has developed a simple and free Javascript calculator that automatically generates the router's default WEP key based on the publicly broadcast default network name. Anderson says gaining unauthorized access to a Verizon FiOS wireless access point "takes as long as it takes you to type in the letters and press enter."
When Open Media Boston spoke to Verizon's FiOS Media Relations and asked about this vulnerability, Manager Cliff Lee said, "I'm not familiar with what you're talking about" and a second call to Verizon's FiOS support line, asking if it was necessary to change the default SSID or WEP key to enhance security seemed to confirm that. In this second call, the support agent did not indicate he had any knowledge of the SSID/WEP vulnerability and again indicated WEP encryption was sufficient:
OMB: The... The router has, um, an SSID and a WEP in it, right?
Verizon Support: Yes. Yes it does.
OMB: Do I need to change those, or is that ok the way it is?
Verizon Support: Um, it's random generation for both of them. Unless somebody has read the information off the side of the router, there's no need to change any of that. Uh, by default it will already be set up. I mean, if you want to change it to something what you were using before, or something completely different, that is entirely your choice.
[Later in the conversation.]
OMB: So the SSID and the WEP will be ok, then, right?
Verizon Support: Yeah, should be fine.
OMB: And that'll... That'll keep anybody from getting onto the network.
Verizon Support: Exactly. They would have to get into your father's home, to the router, read the information and then leave.
[Later in the conversation.]
OMB: All right. Well I... Those were kinda like my only questions 'cause I was looking at it here and just a little worried about setting it up when [my dad] gets back.
Verizon Support: I wouldn't worry about the security. Uh, the biggest issue will be putting in that information into the, uh, laptop or desktop that your father has.
Passwords and Private Data at Risk
Once an attacker has access to the wireless network, Anderson told Open Media Boston, "any plain text protocols (HTTP, AIM, POP, IMAP, FTP, etc.) are available to see. How many of us use the same password for both our email and our sensitive data?" This means once a user's network has been compromised, all unencrypted communications like email, instant messaging and record of web sites a user visits are easily collected.
Furthermore, because Windows firewall "trusts" computers on the same network by default, an attacker who gains access to a Verizon customer's network can then infect any Windows machines not running additional security software with a virus or a worm that can log keystrokes and steal passwords even for encrypted sites, or destroy data on a user's computer.
As the second conversation with Verizon' FiOS support went on, it became clear Verizon's standard installation practices leave customers at an additional risk:
OMB: Should I... Should I change the [router's] login and password when I get it?
Verizon Support: Um, the first time that you log in, it will ask you to change it.
OMB: Ok.
Verizon Support: Uh, Verizon field techs will change it to "password" with the number one at the end.
Hear excerpts from the conversation:
Lee told Open Media Boston that "software on today’s broadband home router requires the Verizon technician to implement password protection as part of the installation process. The customer is provided with the initial password." However, after asking several Verizon FiOS customers to check their router settings, it seems field technicians don't always change the credentials from the router's default, leaving the default username "admin" and the password "password." Even if technicians do change the password to "password1," that password is easily guessable by a human and is included in lists of commonly used passwords that malicious applications will try as part of a dictionary attack.
Again, Actiontec's own support page for the MI424-WR router provides better security advice than Verizon. The page advises users that hackers often try a dictionary attack to guess passwords, so a user's password "CAN NOT be in the form of a real word (like dog or umbrella), they should be random, letters or numbers, [and] capitol letters."
Once in a user's router configuration screen, an attacker can change the default DNS settings to redirect requested URLs of sensitive sites like Bank of America or Gmail to malicious spoofed sitesthat look identical to the originals, in order to capture a user's private login and password credentials.
Protect Yourself: Change Your Default Settings
Users can avoid all of these problems by changing the wireless encryption specification from the default WEP to WPA2 with AES, and by changing the router's credentials to a randomly generated, unguessable password. Read Open Media Boston's comprehensive guide to securing your wireless network for more information.
Home networking security is an increasingly pressing concern for computer users as they store more critical data on computers and conduct private business like banking over the Internet. Most users have little or no understanding of the complexities of networking security and threats, and so rely on professional services to ensure their data and identities are protected. (This is one reason why users purchase security software suites like the Verizon's Internet Security Suite.)
In this context, Verizon's failure to provide its customers with a secure wireless connection by default on its wireless routers, combined with its reluctance to inform its customers of WEP's eight year old vulnerabilities, and its refusal to support WPA seem to contradict Lee's claims that "Verizon takes the security of its customers seriously and continually reviews the security-related elements of its products and services."
Verizon Internet customers may have hope for a more secure future, though. In light of Open Media Boston's investigation, Lee has said "Verizon is reviewing customer documentation and other procedures on this topic."
Support Quality Journalism. Make a Tax Deductible Donation to Open Media Boston
Open Media Boston produces quality investigative journalism on technology, labor, social movements and local politics. But our reporters cannot continue to do so without our readers' help. If you enjoyed this article, please consider making a secure, tax deductible donation to Open Media Boston.


Comments
I just read Jesse Kirdahy-Scalia's investigative report on Verizon and its use of WEP to "secure" home wireless networks. BRILLIANT! I am a Verizon customer with just the Actiontech wireless router mentioned in the article, using WEB, and now I am worried. I called Verizon myself and have been reassured that my sysyem is "secure enough." When I asked support "What does that mean 'secure enough'? And what happens if my neighbor or some driver-by hacks my IP address and downloads child pornography with it?" His response was, "Does anybody hate you that much?" "Hello," I said,"now I won't know that until someone does it, will I?"
Granted, I am really not concerned about my neighbor downloading kiddy porn. She is 86 and doesn't even like kids. But I am concerned about the security of my wireless network. I just received a new Actiontech router from Verizon to replace the old one that burned out and my question is will it enable me to use WPA or WPA2 instead of WEP, and how do I go about setting it up? I was told in a second call to Verizon that "Verizon doesn't support WPA" whatever that means.
Thank you for this terrific article, and I especially enjoyed hearing the recordings. What a great idea to enable OMB readers to hear the exchanges.
JEMS who remains
Sheepless in Seattle...
Yes, for some reason Verizon will not help customers set up a WPA or WPA2 encrypted network. In a followup email, I asked them to comment on this, but received no response. If you're concerned about your network's security and want support from Verizon, let them know. They probably won't change their policies until they hear their customers demand they pay greater attention to security.
To set up your Verizon-provided router with a more secure specification, visit 192.168.1.1 in your browser, enter your username and password (probably either "admin" / "password" or "admin" / "password1" if Verizon techs set it up for you), and click the wireless tab up top. From there, click advanced setup on the left and choose WPA2. Make sure you set a long, randomly generated password.
Read Open Media Boston's guide to securing your wireless network for a more comprehensive review of wireless security issues.