
Secure Your Data Against Unlawful Search and Seizure with TrueCrypt
Computer users who want to protect their files from theft or discovery have many options for encryption. Probably the most secure and flexible of these is TrueCrypt, a cross-platform, open source application that provides on-the-fly encryption of part or all of a disk, and creates totally undetectable encrypted volumes. Get started quickly with this features guide.
There are many scenarios under which your personal data could be compromised: customs agents regularly search the contents of travelers' drives, a computer is reported stolen every 43 seconds, and recent US legislation makes it easier to seize your system if you are suspected of violating IP laws. Modern versions of Windows, OS X and Unix all offer encryption programs and features with their operating systems. However, their features are limited, their methods are detectable, and files encrypted in one operating system may not be readable in another.
It's generally true that the more secure an encryption method is, the less accessible it will be for users. Considering this, it is important to have a flexible encryption solution. TrueCrypt has a broad range of encryption options with varying degrees of security and flexibility, so you are likely to find an option that meets your needs. TrueCrypt creates and formats an encrypted partition in any of the following ways:
- Virtual encrypted disk: Create a dummy file that TrueCrypt will mount as a disk. This file appears to the host operating system just like any other file, and can be moved or copied. The user could email this file to himself or others to clandestinely transport data over a network. When traveling, one could upload this file to a file hosting site like Rapidshare, record the url, delete the original and retrieve the hosted file later, such that the sensitive data does not exist on the user's drive while traveling.
- Encrypted partition or drive: Encrypt part or all of a drive, such as an external disk or flash drive. Bringing your torrented music of movies collection overseas? This option is useful for transporting lots of data on an encrypted, portable drive.
- Encrypted system drive: This is the most secure option. Encrypting your entire system drive means any temporary data or hibernation data is encrypted, as well as all files and folders. The system drive requires password authentication on boot to start up, regardless of what computer it is attached to, making the drive and its data completely secure. TrueCrypt can even encrypt and decrypt a system drive while it is in use, a feature that saves users a great deal of time and hassle.
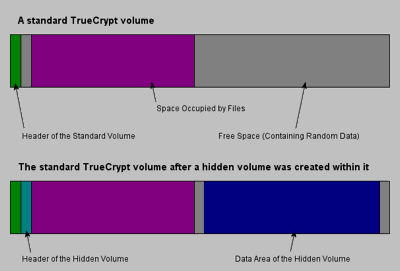
If your system is stolen or searched, TrueCrypt provides two levels of deniability. First, TrueCrypt volumes appear to be random data; while the presence of the TrueCrypt application on one's drive provides circumstantial evidence of a TrueCrypt volume, the data itself cannot be identified as an encrypted volume. Second, TrueCrypt can create a hidden volume or even a hidden operating system inside an existing TrueCrypt volume. As the TrueCrypt plausible deniability guide states, "It may happen that you are forced by somebody to reveal the password to an encrypted volume. There are many situations where you cannot refuse to reveal the password (for example, due to extortion). Using a so-called hidden volume allows you to solve such situations without revealing the password to your volume." In such situations, users can keep the password to the hidden volume secret, and since that volume appears to be random data, there is no way to prove it exists. Extortionists will only see the dummy encrypted volume.
If you're interested in using TrueCrypt, check out the Beginner's Guide and use the application's volume creation wizard to create your encrypted volume. It's easy to follow, and along with theextensive documentation available on the TrueCrypt site, you will quickly and competently complete the process.
Get TrueCrypt and secure your digital life today.


Comments
A few weeks ago I spent too much time looking for a reasonable method for more security for my computer. I decided upon TrueCrypt. I am reassured by Jesse's more knowledgeable endorsement, and only slightly regret the time I spent.
I often spend too much time looking for an application for this function or another. Fortunately, I can use that research for articles, so dead ends aren't a complete loss. I generally feel that if I become frustrated by looking for a solution, it's a good topic to write on.